Artefact/WebServices/WebServicesConfiguration: Difference between revisions
From Mahara Wiki
PiersHarding (talk | contribs) |
PiersHarding (talk | contribs) No edit summary |
||
| Line 57: | Line 57: | ||
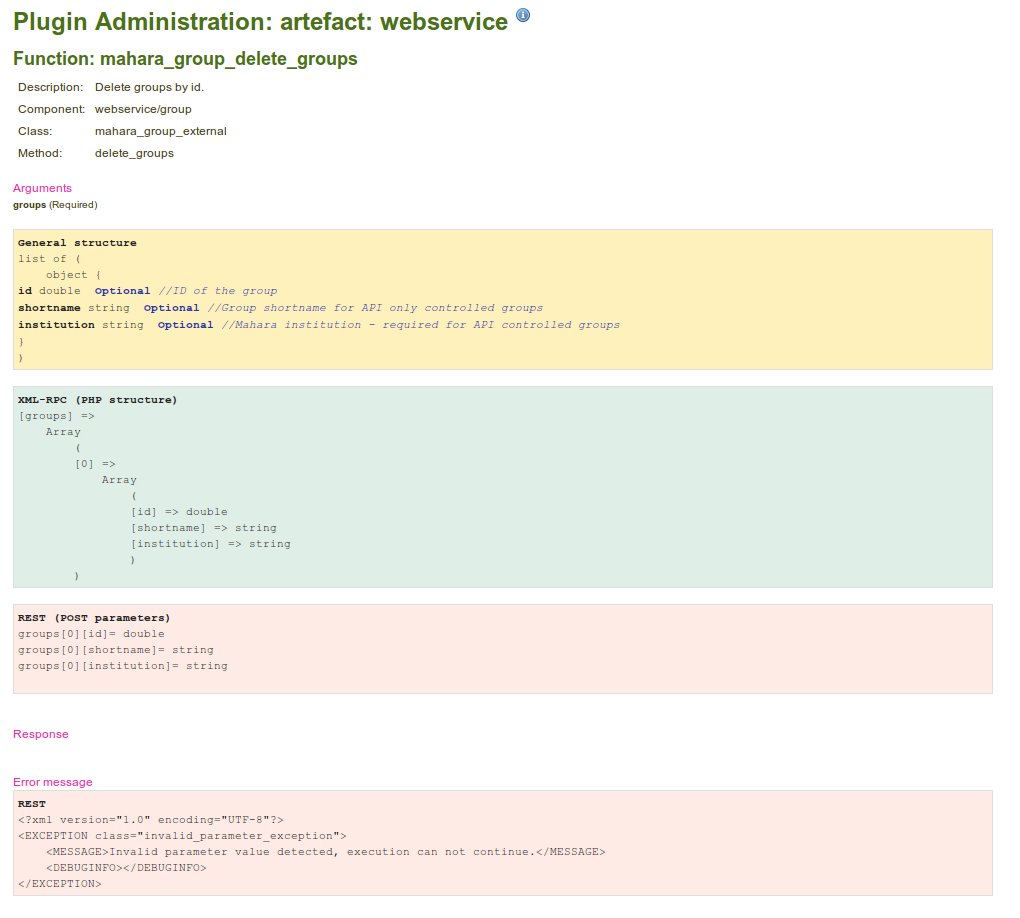
[[File:Webservices-group-delete-api.png|border|Web Services Group Delete API description]] | [[File:Webservices-group-delete-api.png|border|Web Services Group Delete API description]] | ||
=Authentication= | |||
There are currently two forms of authentication for web service access, which are available for all protocols: | |||
* Web Service Tokens | |||
* User/Password based simple authentication | |||
In both cases, the authentication data is passed as query string parameters: | |||
* Token - http://mahara.local.net/artefact/webservice/rest/server.php?wstoken=484dfea8715ed427b4d95796c3013f7d | |||
* simple auth - http://mahara.local.net/artefact/webservice/rest/simpleserver.php?wsusername=blah3&wspassword=blahblah | |||
Note: that the application changes for each - server.php vs simpleserver.php | |||
There is one exception, for SOAP, where the user and password can be passed as part of the Web Services Security Extension SOAP headers (wsse), as plaintext username and password. eg: | |||
<env:Header> | |||
<wsse:Security env:mustUnderstand="1" xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd"> | |||
<wsse:UsernameToken> | |||
<wsse:Username>bean</wsse:Username> | |||
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">blahblah</wsse:Password> | |||
</wsse:UsernameToken> | |||
</wsse:Security> | |||
</env:Header> | |||
== Token Based Access Control == | == Token Based Access Control == | ||
Revision as of 10:08, 23 Haziran 2011
Web Services Configuration
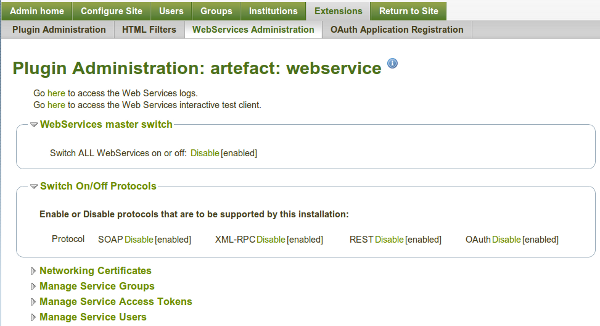
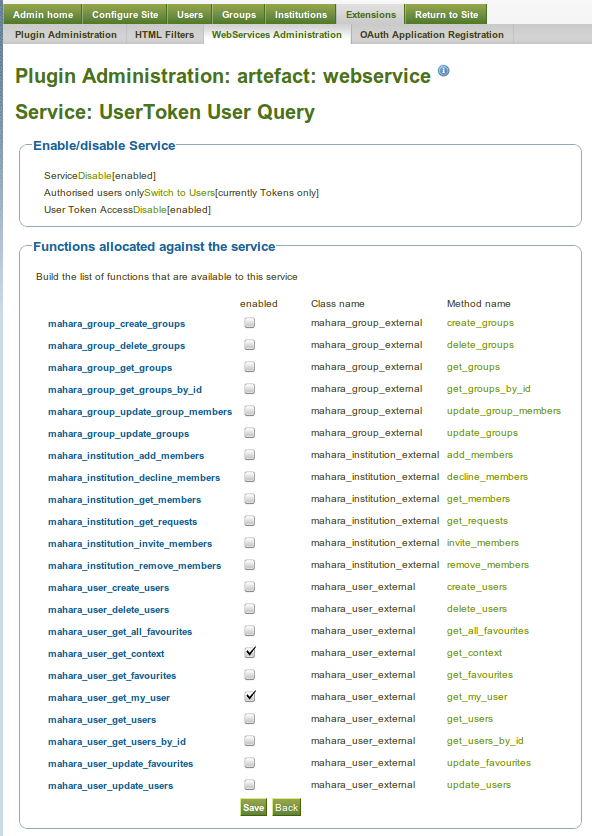
All Web Services configuration hangs off the plugin administration page http://your.mahara.local.net/artefact/webservice/pluginconfig.php
The main page:
From here, you can carry out all the main administrative tasks:
- Globally activate/deactivate web services
- activate/deactivate individual protocols (REST, SOAP, XML-RPC)
- Create Services Groups of Functions that can be accessed
- Generate access tokens, and allocate users, and services groups
- Grant access to users for simple authentication access, and allocate service groups
- look up API descriptions for functions
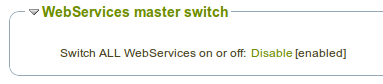
Global activation
Globally activate or deactivate all web service access for when you need to shut off access completely
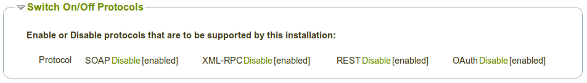
Activating Protocols
Individual protocols can be activated or deactivated. Once activated, the protocol is available to all configured functions/users/tokens.
Available protocols are:
- SOAP
- REST (a basic HTTP and forms POST based interface)
- XML-RPC
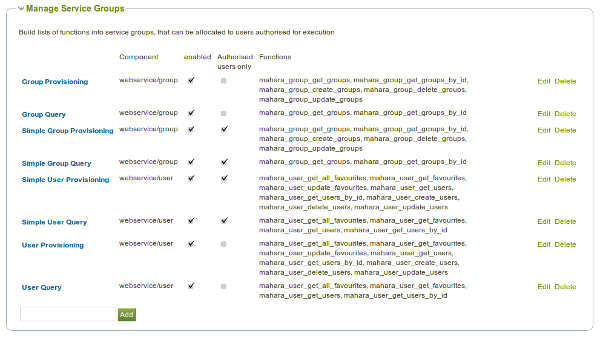
Service Groups
Service groups are the unit of allocation of access to a user (simple auth) or user token. They are a collection of functions.
Give a service group a name, and then specify what functions are to be included. You must also decide what form of authentication can access this service group - web service token, or user simple auth (user and password).
From here, and individual service group can be deactivated for all users.
Function API Descriptions
From the Service Group editing view(above), there is a link to each API function that will take you to a description of the functions API - input/output parameters, and error handling.
Authentication
There are currently two forms of authentication for web service access, which are available for all protocols:
- Web Service Tokens
- User/Password based simple authentication
In both cases, the authentication data is passed as query string parameters:
- Token - http://mahara.local.net/artefact/webservice/rest/server.php?wstoken=484dfea8715ed427b4d95796c3013f7d
- simple auth - http://mahara.local.net/artefact/webservice/rest/simpleserver.php?wsusername=blah3&wspassword=blahblah
Note: that the application changes for each - server.php vs simpleserver.php
There is one exception, for SOAP, where the user and password can be passed as part of the Web Services Security Extension SOAP headers (wsse), as plaintext username and password. eg:
<env:Header> <wsse:Security env:mustUnderstand="1" xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd"> <wsse:UsernameToken> <wsse:Username>bean</wsse:Username> <wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">blahblah</wsse:Password> </wsse:UsernameToken> </wsse:Security> </env:Header>