Plugins/Auth/Saml
From Mahara Wiki
< Plugins | Auth
Authentication plugin for SAML 2.0 based SSO integration. This uses the excellent SimpleSAMLPHP software as a Service Provider.
The plugin is available via the Mahara git repository, and can be found here . General plugin help can be found Plugins.
Install the plugin in /auth/saml.
Ensure the plugin is active under "Administer Extensions".
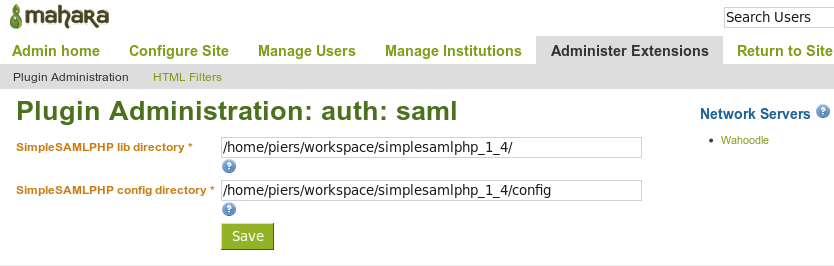
Set the global (site wide) configuration for the Saml plugin by selecting the saml [ Config ] link.
The site wide configuration points to the SimpleSAMLPHP library path, and the associated configuration directory.
It is necessary to configure SimpleSAMLPHP independently of the setup required for the Auth Plugin. The details for this can be found at http://rnd.feide.no/content/using-simplesamlphp-service-provider
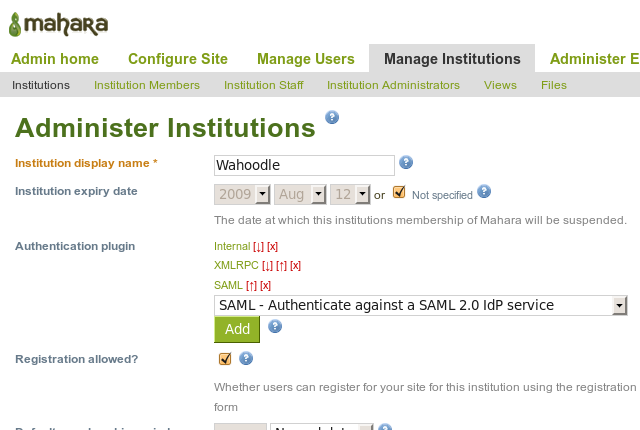
Now we need to perform the institution level configuration. Within each institution, add the SAML 2.0 Identity Provider:
Now, configure the SAML plugin:
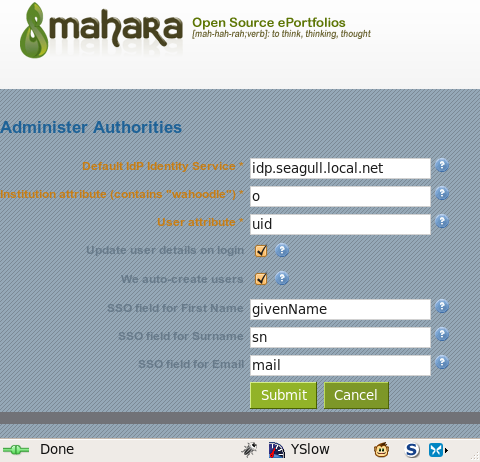
The Identity Service is the one that was configured in the SimpleSAMLPHP metadata/saml20-idp-remote.php file, stripped of the URL decoration down to the hostname like above.
When a user authenticates using SAML 2.0, the Service Provider (SP) negotiates access to a certain list of attributes, that are then made available to the service being accessed (in this case, Mahara). One of these attributes must hold the institution name/id of this institution being configured against. In this case the Mahara institution has an id of "wahoodle", and thie "o" user attribute is the institution attribute allocated to the user that we are expecting to find the institution name in - namely "wahoodle" in this instance.
This enables one Identity Provider using varying attribute names, and values, to map users to different Mahara Institutions.
Typically the Identity Provider (IdP) is backed by an LDAP directory for the user attribute store, so in the above example the attribute names being mapped look just like common LDAP ones.
User attribute maps the IdP attribute to the mahara "
Username for external authentication
".
Update user details on login will mean that the following 3 attribute mappings get updated from the values supplied by the IdP, everytime a user logs in.
We auto-create users allows the auto creation of Mahara accounts upon user first contact.
In order to trigger the use of SAML based authentication, point the browser at http://[mahara service location]/auth/saml/ - this is the launch URL that you would use as the navigation integration point for other services to connect to Mahara.